TrickBot has evolved over the last 4 years to become a serious threat against our organization. In September 2020, TrickBot played a significant role in the delivery of Ryuk ransomware that resulted in the largest ransomware attack against hospitals. Shortly after that attack, the US Cyber Command eliminated nearly 90% of TrickBot’s infrastructure. By the end of October, we began seeing levels of attacks consistent with attacks from August 2020. After the Russian government raided the developers of Dyre banking trojan, TrickBot was built using updated and modified Dyre code. It appears that this recent infrastructure takedown has motivated some changes to TrickBot. More recent attacks have seen significant improvements including targeting Linux, sandbox avoidance techniques, as well as attacks against BIOS.
TrickBot Relationships
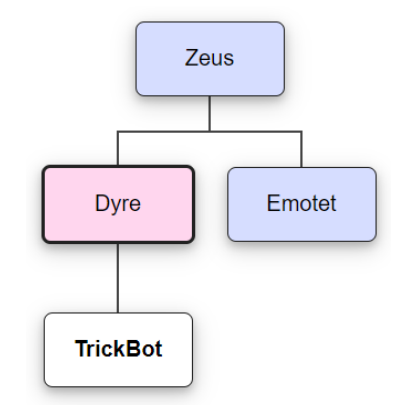
TrickBot was first identified in 2016 and shared very similar code structure as the former Dyre banking malware. Dyre was primarily known for stealing banking credentials from infected users and TrickBot had similar capabilities. This functionality caused TrickBot to be categorized as a banking trojan.
Notable Events
Over the years TrickBot integrated additional features to expand beyond a banking trojan. Within a year of TrickBot’s emergence, developers added a self-propagating worm to help spread across infected networks. More recently, it has been seen to implement anti-analysis techniques to deter malware analysis and detection. In September of 2020, TrickBot was used to deliver ransomware to U.S. hospitals in the largest ransomware attack to date. Shortly after this attack, TrickBot infrastructure was almost entirely dismantled, allegedly by the U.S. Cyber Command. Attacks dropped significantly following this, however, TrickBot has been seen since the takedown.
Analysis
Delivery
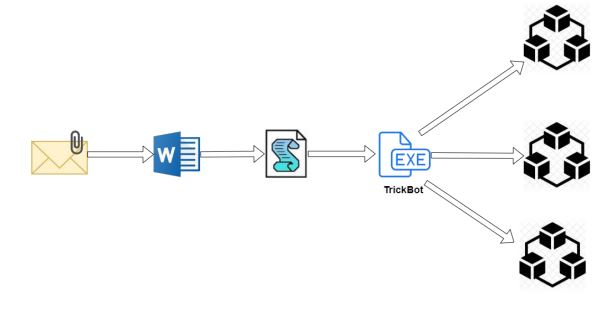
TrickBot is most often delivered through email campaigns with malicious Microsoft attachments.
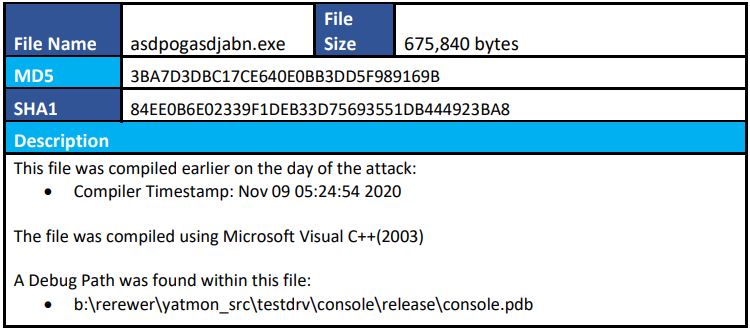
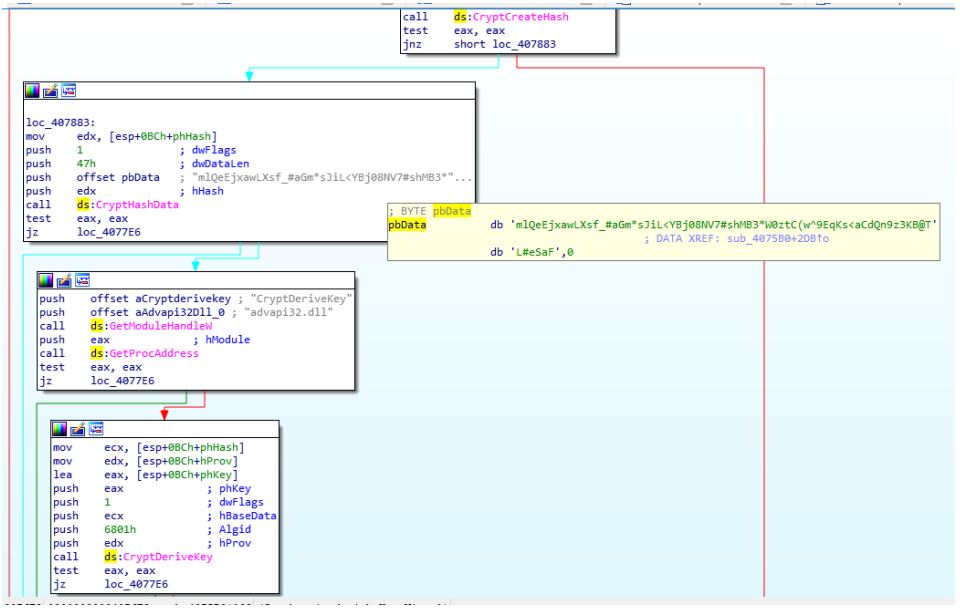
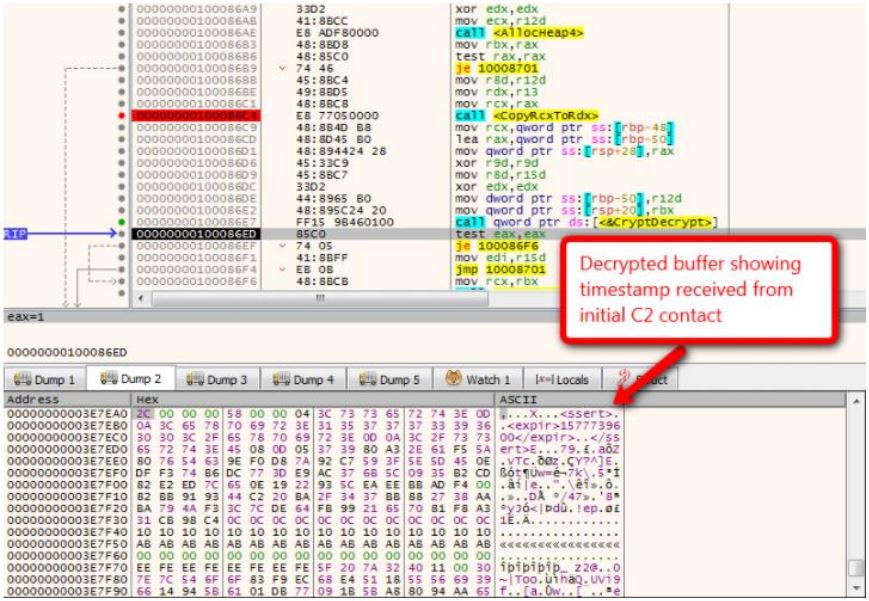
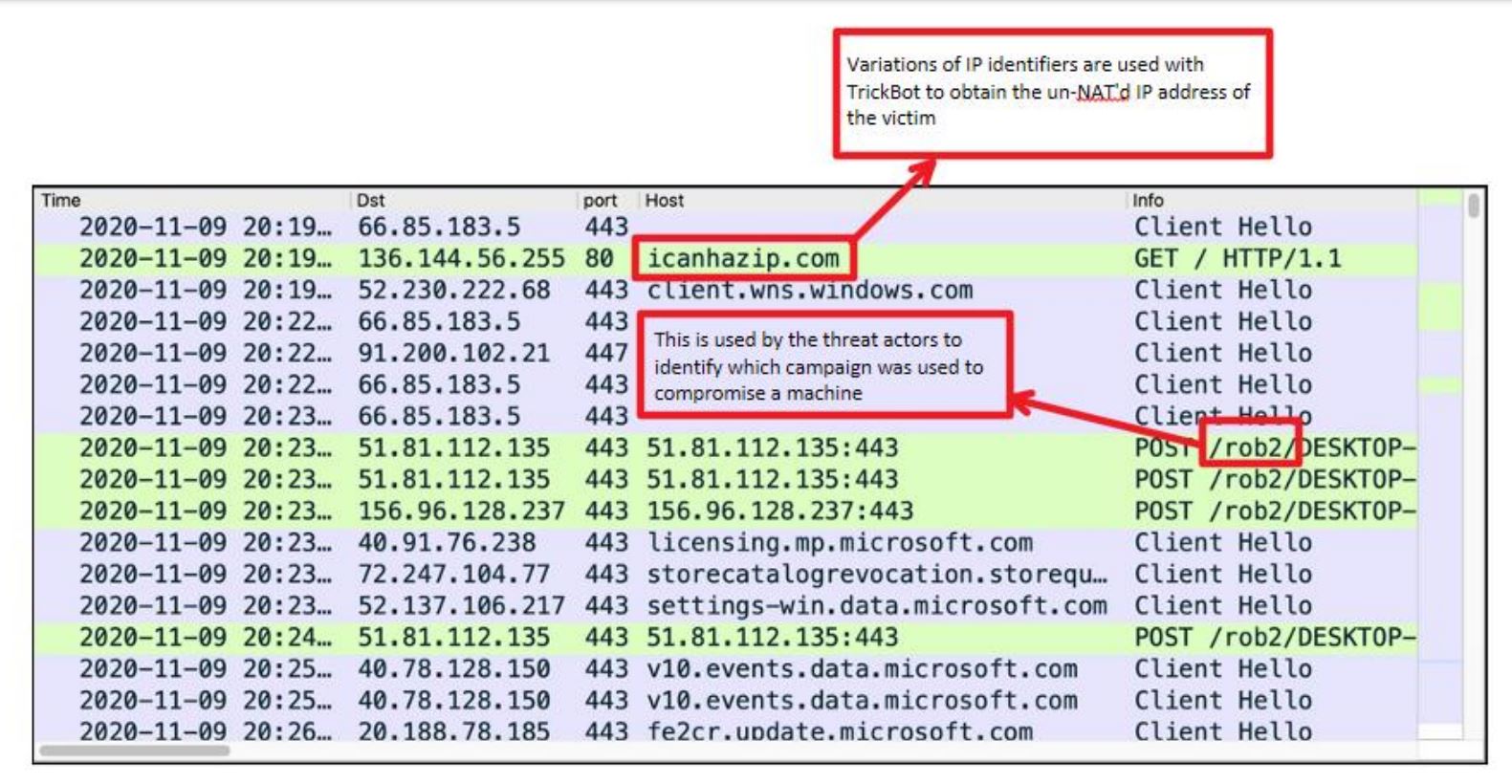
Malware Analysis
Recommended Actions
- Block WSCRIPT and ActiveX in Microsoft Office/PDFs
- Restrict non-Microsoft signed code and dynamically-generated code [1]
- Disable Extension Points [2]
- Disable SMBv1